Development Livin' the Thug... Err... VPN Life
Depending on who you talk to, a Virtual Private Network (or VPN) is either the greatest thing since sliced bread, or a tool of the devil. I like to think it’s more in the middle. Actually, the only devilish part is in the details of setting it up… After that, it’s pretty great.
There are many paid services that will enable you to connect to a VPN to encrypt your traffic. ExpressVPN, IPVanish, HideMyAss, and a number of others (note: those are not affiliate links, and I can’t recommend any of their services - as I don’t use them, just the major players that I know about).
Although, what I will say is that if a VPN service you want to use doesn’t use HTTPS on their website - I would probably run… That kind of laziness from a company selling privacy/security tools speaks for itself.
I Hate VPN Companies
I don’t know why, and I have absolutely no good reason, but I don’t really trust VPN companies… There’s a certain amount of centralization of trust that I’m just not willing to give to a random company who I otherwise would have no interaction with. Caveat to this is that I’m aware that Google is reading my emails… But whatever, everyone has their own thing I guess - and this is mine.
Maybe it’s because of stuff like this, but I doubt it, as I literally just found that link.
It goes so far that this is what I wrote about the subject to a colleague the other day: “I’ve never wanted to use those paid VPN services, as I trust them as much as I do as the schmuck sitting next to me at Starbucks.”
Where did that come from, you ask? No idea. Unfair? Probably. Will I change? No dice homeslice.
So, what do we do?
Well… Let’s do what we always do. Build it ourselves!
Thanks to the magic of the internet, as served by Digital Ocean, we can build a VPN for just $5/month - click here for my referral link to get $10 of credits when you sign up.
There are a bunch of steps here, but it basically goes as follows: Harden the server, continue to harden the server, setup the VPN, test the VPN, sleep like a baby wearing a privacy Snuggie wrapped in a blanket of encryption.
Note: Referring back to my over-description, there should be an asterisk next to the ‘privacy’ statement… More like… Better than normal privacy, but NOT anonymity.
But first, let’s go back to basics.
What is a VPN?
This image from a Hotspot Shield post offers a good example of what a VPN is.
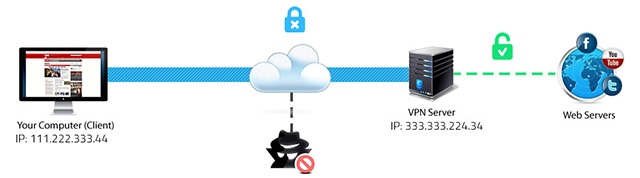
I also like this PC World visual description:
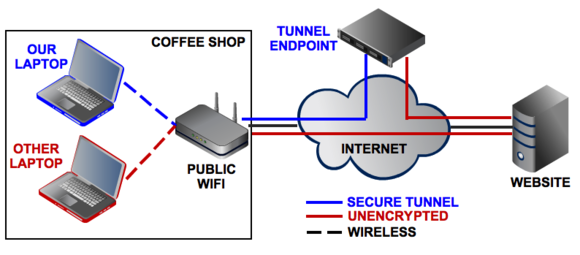
Additionally, TheBestVPN created an in-depth, de-jargonized VPN Beginners Guide which is worth a read (I have pinged them about adding ProtonVPN to their guide as well).
The salient point is that a VPN gives you an encrypted virtual tunnel to your VPN server, which then exposes your traffic to the rest of the world. The idea being that your VPN server has better security than (for example) the Starbucks WiFi network you happen to be on while reading this.
The reason this is probably true is because a typical coffee shop/airport/hotel WiFi network is unencrypted, leaving all of your data out in the open for anyone to see.
By the way, are you using HTTPS Everywhere yet? No? DOWNLOAD IT!
The reason I say that is because the goal is to have end-to-end encryption (as much as we can reasonably manage anyways). I want my data to be encrypted as close as possible to my computer to as close as possible to the target website. HTTPS facilitates this, as both you and your target site negotiate an encryption scheme.
A VPN doesn’t negate the need for HTTPS either… You MUST use HTTPS, and SHOULD use a VPN.
What isn’t a VPN?
Many things…
But, for the context of this post, it is NOT an anonymity tool. I don’t care what anyone tells you, a VPN on it’s own won’t make you anonymous. It will give you a level of privacy you wouldn’t otherwise have, but you’re absolutely not anonymous.
If you’re looking for anonymity, TOR is a step closer to that, but even then you’re not as anonymous as you think. Also, I look for any excuse to link to Mr. Robot.
Conveniently, I found a nice Top 10 VPN myths page - from a company trying to sell their VPN services, nonetheless…
Differences Between TOR and a VPN
I just can’t beat this explanation from an excellent StackExchange post.
Example Time
To help solidify the differences between the possible schemes, let’s use an example.
Let’s pretend you’re at a Starbucks using their Wifi network. You navigate to ‘http://i-have-an-embarrassing-medical-condition.com’, go to their ‘Make an appointment’ form, fill in your name, phone number, address, and ask for an appointment next Sunday at 2pm to discuss your… well… embarrassing medical condition.
A malicious user at that Starbucks scanning network traffic would then have your name, phone number, address, and know you wouldn’t be home at 2pm on Sunday. Best case, they sell your data to spammers, slightly worse they use a phishing attack, and much worse - you arrive Sunday night to a freshly burgled home. All because you used an insecure network and no encryption.
Imagine that same scenario, but the only difference was that you put an ‘s’ after HTTP… Well, a malicious user on the network could still see that you went to ‘https://i-have-an-embarrassing-medical-condition.com’, which is embarrassing as all hell… But, that’s really it. If the site handled forms correctly, all of your personal information would look like gibberish thanks to encryption.
Finally, let’s use a VPN. A malicious user would see… Well, nothing. They would see that you’ve connected to a server somewhere, but the traffic would be meaningless gibberish, and since all data is piped through that remote server, the malicious user couldn’t see WHICH websites you’re connecting to either.
In this last scenario, the VPN server is now the entity which can see the HTTP or HTTPS traffic as described above. But, I mentioned before, we’re assuming that the VPN server is ‘trusted’ (assumed to not be malicious). In the VPN service industry, you’ll see lots of mentions to logging and no-log companies (most of whom are probably lying about not logging).
But, here is where we come back to the idea of centralizing that trust… How do I know those VPN companies (and more importantly, their employees) are any more trustworthy than the malicious user on my Starbucks Wifi network?
Please note that for simplicity, I’m not discussing what ISPs or federal agencies can track or trace using their own methods (deep packet inspections, DNS leakage, controlling internet backbones, etc…). That is can of worms territory.
What’s Next?
Well, this post was originally going to talk about hardening your server, in preparation of installing a VPN - but I think that’ll need to wait for next week, as I digressed a bit further than I had expected.
To finish up, I think I’ll leave off with a scare tactic, which seems to be popular with lots of VPN providers…
Umm… Let’s see… Don’t use the internet without a VPN, you may be in grave danger!
P.S. Fun, but depressing, hobby: Opening up an unsecured Wifi network called “I-Read-Your-Email” and watching how much traffic comes through… So, so sad.
Feature Photo credit: Yuri Yu. Samoilov / Foter / CC BY